DSP Authentication¶
The Yahoo DSP API uses the OAuth 2.0 protocol as a simple and secure method for handling authentication and controlling access.
Note
To enable the DSP API for your account, reach out to your Account Manager or Product Support and have them create an internal ticket with the email address of the account to be enabled.
Important
If the DSP API has not been enabled for your account, a message will display that states the Client ID and Client Secret are “undefined.” Reach out to your Account Manager or Product Support and have them create an internal ticket with the email address of the account to be enabled.
Note
These instructions assume the user is already created in the DSP UI. If you need to create a new user, refer to Manage Users in the DSP UI help center.
Once the DSP APIs are activated, follow the steps to create an OAuth2 client of DSP. The client ID and client secret that you generate through this process are required to access Yahoo DSP API.
1 Get Your Client id and Client Secret
Get Your Client id and Client Secret¶
As a security measure the DSP UI only displays the client ID and secret once. If you lose your client ID and secret, reach out to DSP Support to obtain a new one.
Open the DSP UI.
In the upper-right corner of any DSP page, select your name. For example:
Select My Account from the list.
Select the Activate button.
A terms of service message displays.
Select Agree.
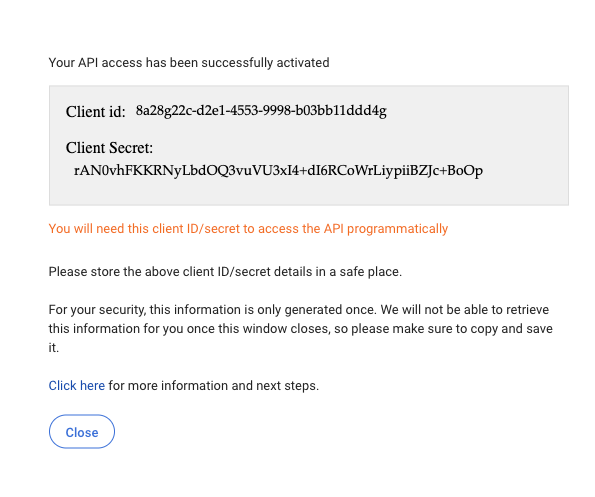
A success message displays. The message includes your client ID and secret.
Important
If the DSP API has not been enabled for your account, a message will display that states the Client ID and Client Secret are undefined.
Copy the client ID and secret, and keep it in a safe place. You’ll need it later.
Note
Your client ID and secret are for your use only. For security purposes, if you suspect that someone other than you has obtained your client ID and secret, contact DSP Support immediately.
Select Close to close the success message.
Generate the Access Token¶
DSP uses OAuth2 for API authentication and authorization. The next step is to generate an access token using the client ID and secret provisioned above.
Once you generate the access token, you can access DSP REST API’s by passing the following two additional headers in the request.
Header |
Value |
Description |
|---|---|---|
X-Auth-Method |
OAuth2 |
The authentication method to use for accessing DSP. The value should always be OAuth2 for API access. |
X-Auth-Token |
Use client ID and secret to generate access token. |
The value is the access token the JWT generates using the client ID and secret (refer to steps below). |
About Access Tokens¶
DSP Uses the OAuth2 client_credentials workflow and identifies the client using a JSON Web Token to generate the access token. Complete the following two steps to the access token using the client ID and secret.
Note
You don’t need to follow these steps manually. There are many robust scripts available in almost all the popular languages which will automate the above JWT generation based on the input provided.
You can find a list of popular libraries at JWT. Be sure to choose one that supports HS256. Provide it the values defined below and it will generate the JWT for you.
Generate JSON Web Token¶
The OAuth2 client_credentials workflow uses a JSON Web Token (JWT) to identify the client. A JWT primarily consists of three parts:
Header - Normalized structure specifying how the token is signed.
A free set of claims.
A signature to ensure data integrity.
For Yahoo DSP, use the following values:
Header¶
{ "alg" : "HS256" "typ": "jwt" }
Payload¶
{ "aud": "https://id.b2b.yahooinc.com/identity/oauth2/access_token?realm=dsp", "iss" : "<client_id>", "sub": "<client_id>", "exp" : <Expiry time as Unix Epoch in seconds>, "iat" : <issued at time as Unix Epoch in seconds>, "jti" : <UUID Unique identifier for the JWT> }
Signature¶
{ "signature" : "<signature generated using HS256 algorithm, see below>" }
Generate the signature as follows:
jwt_signing_string = base64url_encode(header) + ‘.’ + base64url_encode(body) jwt_signature = base64url_encode(hmac_sha256(jwt_signing_string, client_secret)) final_jwt = jwt_signing_string + ‘.’ + jwt_signature
The final JWT looks something like this:
ew0KICAiYWxnIjogIkhTMjU2IiwNCiAgICJ0eXAiOiAiSldUIg0KfQ.ew0KICAiYXVkIjogIntwcm90b 2NvbH06Ly97YjJiLmhvc3R9L2lkZW50aXR5L29hdXRoMi9hY2Nlc3NfdG9rZW4/cmVhbG09PHlvdXIt cmVhbG0+IiwNCiAgImlzcyI6ICJ7Y2xpZW50X2lkfSIsDQogICJzdWIiOiAie2NsaWVudF9pZH0 iLA0KICAiZXhwIjog4oCce2V4cGlyeSB0aW1lIGluIHNlY29uZHN94oCdLA0KICAiaWF0Ijog4o Cce2lzc3VlZCB0aW1lIGluIHNlY29uZHN94oCdDQp9DQo.uKqU9dTB6gKwG6jQCuXYAiMNdfN Rw98Hw_IWuA5MaMo<base64url-encoded header>.<base64url-encoded claims>.<base64url-encoded signature>
Note
They are separated with a “.”
Generate a JWT Access Token¶
Once you generate a JWT, you can use it to generate the access token using the Yahoo DSP.
Important
You don’t need to generate an access token for each call. Be sure to reuse your tokens before the expiry time. If your application caches an access token until its expiry, then set it up to be regenerated within that amount of time.
The expiry time should be less than 24 hours, but Yahoo recommends setting it for one hour.
Request¶
POST https://id.b2b.yahooinc.com/identity/oauth2/access_token
Headers¶
“Content-Type” : “application/x-www-form-urlencoded” “Accept” : “application/json”
FORM Parameters¶
Field Name |
Value |
Description |
|---|---|---|
grant_type |
client_credentials |
The value is literal ‘client_credentials’ |
client_assertion_type |
The value is literal urn:ietf:params:oauth:client-assertion-type:jwt-bearer |
|
client_assertion |
JWT Generated |
The JWT generated in the procedure above. |
scope |
dsp-api-access |
The scope is literal dsp-api-access |
realm |
dsp |
The value is literal ‘dsp’ |
Sample ‘curl’ Command¶
Here is a sample curl command for generating the access token:
curl "https://id.b2b.yahooinc.com/identity/oauth2/access_token" \ -X POST \ -H "Content-Type: application/x-www-form-urlencoded" \ -H "Accept: application/json" \ -d "grant_type=client_credentials&scope=dsp-api-access&realm=dsp&client_assertion_type=urn:ietf:params:oauth:client-assertion-type:jwt-bearer&client_assertion=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhdWQiOiJodHRwczovL2lkLmIyYi52ZXJpem9ubWVkaWEuY29tL2lkZW50aXR5L29hdXRoMi9hY2Nlc3NfdG9rZW4_cmVhbG09ZHNwIiwiaXNzIjoiMTk3MDMxZTgtMTU0Ni00MTBmLTg0ZTMtY2Q2YzM4ZGJjZWMwIiwic3ViIjoiMTk3MDMxZTgtMTU0Ni00MTBmLTg0ZTMtY2Q2YzM4ZGJjZWMwIiwiZXhwIjoxNjIzNDQzNDAyfQ.HksbyvWXlvfbs3XI5Y_u50eWPiNc2-Qa2B4eGXLN6A"
Sample Response¶
{ "access_token" : "3f94eb47-a295-4977-a375-e27bea5c828b", "scope" : "dsp-api-access", "token_type" : "Bearer", "expires_in" : "599" }
Access the API¶
Once you have generated the access token, you can access Yahoo DSP by passing it in the ‘X-Auth-Token’ header along with the ‘X-Auth-Method : OAuth2’ header.
For example, to access the traffic API:
curl "https://dspapi.admanagerplus.yahoo.com/traffic/dictionary" \ -H "X-Auth-Method: OAuth2" \ -H "X-Auth-Token: 3f94eb47-a295-4977-a375-e27bea5c828b"
FAQs¶
Q: What is the expiration time for the access token?
A: The token expiration is controlled by the client. The maximum allowed is 24 hours. Yahoo recommends that clients use a 10-minute expiration for greater security.
Q: Can I use a Yahoo corporate account to use IDB2B Oauth flow?
A: Yes.